What is a proxy IP?Where can proxy IPs be applied?
What is a proxy IP?

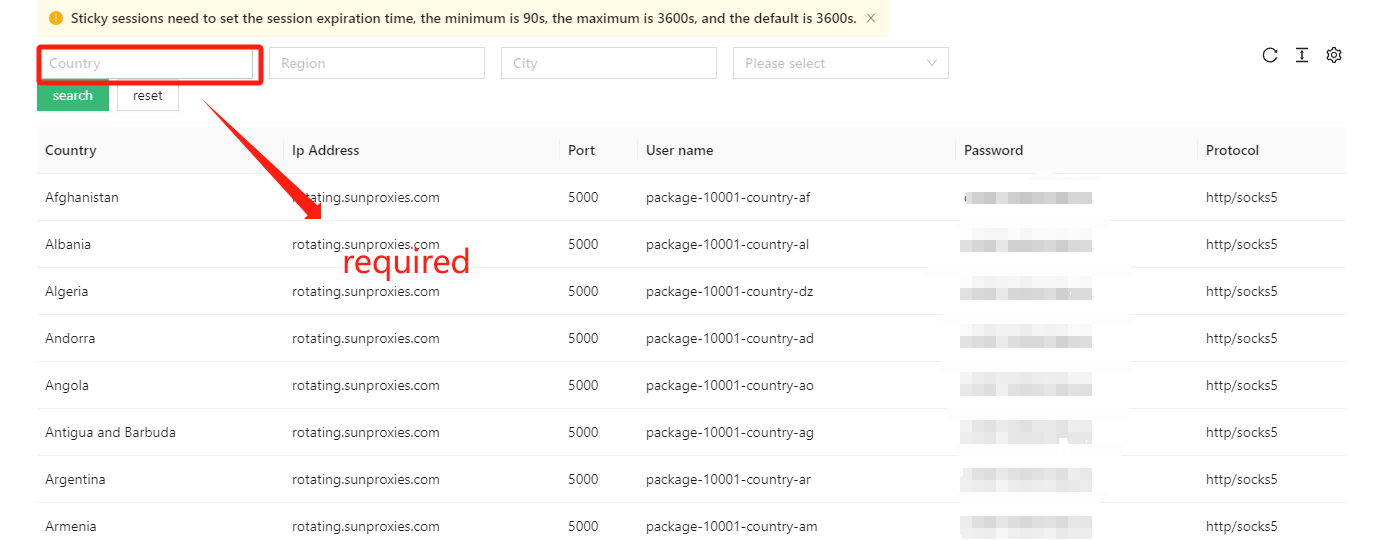
A proxy IP (Proxy IP) refers to an IP address used for network access through a proxy server. The proxy server can shield the user’s real IP address, allowing them to anonymously access the internet. Proxy IPs can be divided into three types: transparent proxy, anonymous proxy, and high anonymous proxy.
Transparent proxy: In the case of using a transparent proxy, the user’s real IP address will be passed on to the target server. The target server can know the user’s real IP address and the detailed information of the access request.
Anonymous proxy: In the case of using an anonymous proxy, the user’s real IP address will be hidden, but the target server can know that the user is accessing through a proxy server.
High anonymous proxy: In the case of using a high anonymous proxy, the user’s real IP address will be hidden, and the target server cannot know that the user is accessing through a proxy server.
Proxy IPs are commonly used to hide the user’s real IP address, bypass geographic restrictions, access blocked websites, and improve access speed. At the same time, proxy IPs may also be used for illegal activities such as cyber attacks and fraud. Therefore, when using proxy IPs, it is necessary to carefully select trusted proxy servers and comply with relevant laws and regulations.
Where can proxy IPs be applied?

Proxy IPs can be applied in the following scenarios:
Privacy protection: Proxy IPs can hide the user’s real IP address, provide anonymity, and protect the user’s privacy.
Bypassing geographic restrictions: Some websites or services may restrict access from specific regions. Using proxy IPs can bypass these geographic restrictions and access restricted content.
Web scraping: Proxy IPs can be used for web scraping. By using multiple proxy IP addresses for crawling, it can avoid being banned by the target website.
Accelerating access: Using proxy IPs allows users to choose high-speed proxy servers, thereby improving network access speed.
Data collection: Proxy IPs can be used for data collection. By using multiple proxy IP addresses, it can avoid being identified and banned by the target website.
Testing website access: When developing and testing websites, proxy IPs can be used to simulate different geographical locations and IP addresses to verify website access in different environments.
It should be noted that when using proxy IPs, it is necessary to comply with relevant laws and regulations and avoid engaging in illegal activities such as cyber attacks and fraud.
What are the most widely used scenarios for proxy IPs?

The most widely used scenarios for proxy IPs mainly include the following aspects:
Privacy protection and anonymous browsing: Proxy IPs can hide the user’s real IP address, protect personal privacy, and prevent personal information from being tracked and collected. Using proxy IPs in browsing web pages, sending emails, and other activities can achieve anonymous browsing and protect personal identity.
Bypassing geographic restrictions: Some websites or services may restrict access from specific regions. By using proxy IPs, users can change their geographic location, bypass geographic restrictions, and access restricted content.
Web scraping and data collection: Proxy IPs can be applied to web scraping and data collection. By using multiple proxy IP addresses, it can avoid being banned by the target website, improving crawling efficiency and stability.
Network security and defense: Proxy IPs can be used for network security and defense. By acting as an intermediary, the proxy server can hide the real IP address of the server, improving server security and defense capabilities.
Accelerating access and load balancing: By selecting high-speed proxy servers, network access speed and response time can be improved. At the same time, proxy IPs can also be used for load balancing, distributing requests to multiple proxy servers, improving system performance and stability.
It should be noted that when using proxy IPs, it is necessary to comply with relevant laws and regulations and avoid engaging in illegal activities such as cyber attacks and fraud.
Where can proxy IPs be obtained?
Proxy IPs can be obtained from the following sources:
Proxy service providers: There are many providers specialized in offering proxy IP services. Users can obtain proxy IPs through purchase or subscription. These service providers usually offer stable and reliable proxy IP resources, allowing users to choose suitable proxy IPs according to their needs.
Free proxy IP websites: Some websites provide free proxy IP lists, allowing users to obtain free proxy IPs from these websites. However, the quality and stability of free proxy IPs may not be as good as those provided by paid service providers, so caution is advised when choosing.
Crawling and verification: Users can write crawler programs to crawl proxy IP resources from the internet and perform verification and filtering. This method allows obtaining a large number of proxy IPs but requires programming skills and time investment.
Regardless of the source of obtaining proxy IPs, the following aspects should be considered:
Stability and reliability: The stability and reliability of proxy IPs are crucial for user experience and effectiveness. Choosing reputable and well-known service providers or websites can improve the quality of obtained proxy IPs.
Privacy and security: When using proxy IPs, attention should be paid to personal privacy and data security. Avoid using proxy IPs from unknown sources or engaging in illegal activities to prevent risks to personal privacy and data.
Geographical location and protocol: Selecting appropriate proxy IPs according to specific needs, including required geographical locations and supported protocol types (such as HTTP, HTTPS, SOCKS, etc.).
In summary, obtaining proxy IPs requires selecting suitable channels based on individual needs and actual situations, while paying attention to the quality and security of proxy IPs.