Various uses of proxy IP
Proxy IP (Proxy IP), as a network technology, has various application scenarios and uses. This article will introduce several common uses of proxy IP, including network access, data collection, security protection, etc.
1. Browse anonymously and protect privacy
Using a proxy IP can help users hide their real IP address, thereby realizing anonymous browsing and protecting personal privacy. In some cases, users may not want to reveal their real identity and location information. By using a proxy IP, the user’s real IP address is replaced by the proxy server, thereby making the user anonymous. This is useful for avoiding malicious tracking, ad targeting, and more.
2. Break through network restrictions and access blocked content
From time to time, users may encounter network restrictions or firewall issues that prevent direct access to certain websites or services. By using a proxy IP, users can bypass these restrictions in order to access blocked content normally. By choosing a proxy server located in another country or region, the user can simulate being in that region, thereby obtaining the lifting of access restrictions.
3. Accelerate network access speed
In international network access, the access speed may be slow due to the long distance of the network and other reasons. By using a proxy IP, users can choose a proxy server located at the location of the target server, thereby speeding up network access. The proxy server acts as a transfer station, forwards the user’s request to the target server, and returns the response to the user, reducing the delay of data transmission.
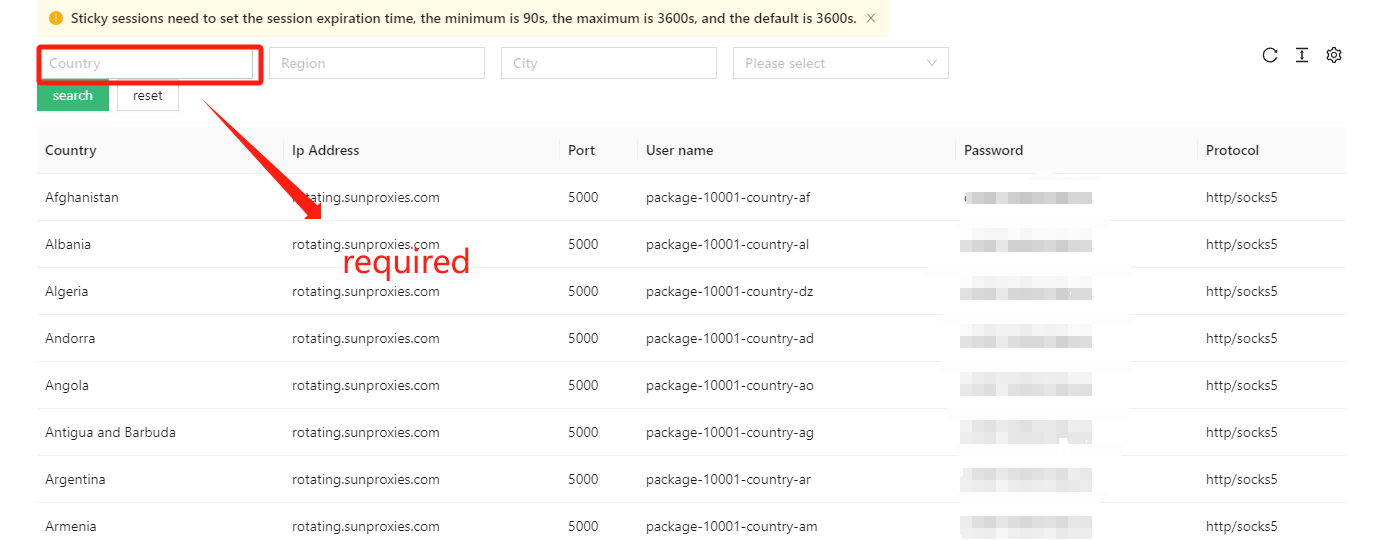
4. Data Acquisition and Validation
Proxy IP is also commonly used for large-scale data collection and verification. When conducting large-scale data collection of target websites during the same time period, using multiple proxy IPs can spread requests and mitigate the risk of a single IP address being banned. In addition, by constantly switching the proxy IP, you can verify whether a service or website has restricted crawlers.
5. Security testing and protection
In network security testing, the use of proxy IP can simulate the behavior of attackers. For example, in penetration testing, red teams can use proxy IPs to launch attacks to assess the security of the enterprise itself and fix potential vulnerabilities in a timely manner. At the same time, the proxy IP can also be used for reverse protection. Enterprises can set up proxy servers to filter and monitor inbound and outbound network traffic to protect their own network security.
To sum up, proxy IP has multiple uses such as anonymous browsing and privacy protection, breaking through network restrictions, accelerating network access, data collection and verification, and security testing and protection. Understanding these uses can help us make better use of proxy IP technology, thereby improving network experience and data security.
Hope this article helps you! If you have other questions, feel free to continue asking.